
UFS Explorer Technician
- The widest range of supported storage technologies
- Broadest file system coverage among data recovery products
- Multi-pass disk imager with advanced processing of read defects
- Support of forensic disk images of various formats
- Configurable disk reading procedure
- Integrated algorithms for disk and file decryption
- Automatic recognition of metadata of hardware and software RAID
- Versatile RAID Builder with an internal script handler
- Multiple tools for work with SAN-class storages
- Extensive reporting options, including files integrity control
- Licensed only to business customers
Overview
UFS Explorer Technician is designed for our most demanding business customers facing the most complex tasks and rare data storage technologies. We have included the widest list of supported file systems in this product, even compared to products from other vendors. This also applies to the list of supported data storage systems.
When starting work on a task, you need to create disk images to prevent data corruption or hardware failure. UFS Explorer Technician not only allows you to quickly and accurately create disk images thanks to the presence of a multi-pass disk imager, but also supports hardware write blockers from various vendors that guarantee data integrity and protect it from damage. The program also supports the creation of "full" disk images for non-standard sector sizes, which allows you to apply post-processing of extended sector data (for example, for NetAPP). It is also possible to create images with integrity control (E01 format) for further work with them as digital evidence.
When the images are ready for processing, the program allows you to work with them in the same way as with the original disks: assemble data volumes, search for lost data, etc. Disk images created by programs from the UFS Explorer family as well as programs from other manufacturers, including competitors, are supported.
The program supports a large number of tools for assembling volumes created by various technologies: from simple volumes or RAID volumes to multi-tier, thin-provisioned volumes. When the required tool is not available, it can be added through the plugin mechanism. At the same time, it is not necessary that the plugin was developed by us: a simple and universal interaction mechanism allows you to develop your own plugins.
When the volume is assembled, you can immediately access the data of the file system: the program implements "reading" of all supported file systems. If you need to find lost data or reconstruct metadata after damage, the program supports several modes of volume analysis (scanning), including fast (indexing) and deep scanning.
If the data is encrypted, the program will be able to decrypt it by supporting a large number of popular encryption methods, including BitLocker, LUKS, Apple encryption and so on. Of course, this is only possible if you have the appropriate passwords or encryption keys.
Found data can be processed and sorted in the interface, supported file-level encryption can be decrypted and data can be copied to another medium. Moreover, data copying can be started both manually (file by file, directory by directory), and in automatic or batch modes. In any case, the program not only copies data, but also preserves file attributes. It also has extended support of reports, including file hashes report.
If you only need to assemble a volume for processing by other software, this is also quite easy to do: the program allows you to mount the assembled volume in the OS as a virtual SCSI disk.
UFS Explorer Technician has more strict licensing comparing to other UFS Explroer software to reduce the factor of software piracy. For this reasons the software is only licensed to business customers. The following options of the software activation are available:
Software activation options
 Software Registration Code
Software Registration Code
A unique alphanumeric code issued on the basis of the submitted user’s System ID, which should be entered in the program’s interface.
 Hardware-based Access Key
Hardware-based Access Key
A Sentinel HL key on a USB-device that enables running the software when physically connected to the computer.
- Can be transferred between different machines
The details related to the usage of different types of Access Keys along with other licensing terms and conditions are available in the End-User License Agreement.
A demonstration license for the software is provided using a "Software Registration Code" upon request by a customer or a potential customer. A full license is granted after its payment for a certain time (from one to five years) and can be based on a "Software Registration Code" or devivered physically with a "Hardware-based Access Key". The second option requires an additional commission, but it is possible to transfer the license between workstations; renewal of such a license in the presence of a working token does not require an additional fee.
Technical specifications
General: FAT, FAT32, exFAT
Windows: NTFS, ReFS/ReFS3
macOS: HFS+, APFS
Linux: Ext2, Ext3, Ext4, XFS, Extended format XFS, JFS, ReiserFS, Btrfs, F2FS
BSD/Solaris: UFS, UFS2, Adaptec UFS, big-endian UFS, ZFS volumes
VMware: VMFS, VMFS6
QNAP QuTS hero: QZFS
NetAPP ONTAP: WAFL (versions 2 to 4)
macOS: HFS
Novell: NWFS, NSS, NSS64
IBM/Microsoft: HPFS
AIX: Legacy JFS1, JFS2 Current Unix.: VxFS4, VxFS6, VxFS7
Older Unix: EAFS, HTFS, DTFS
Urive: NxFS CD/DVD/media: ISO9660/Joliet, UDF
Logical Disk Manager, Storage Spaces, Microsoft volume deduplication, Apple Core Storage, Apple Software RAID, LVM, mdadm, supported hardware and software RAID metadata.
MBR, Apple Partition Map, BSD/Adaptec/Solaris/Unix Slice Map, GPT, Novel, RAID
Providing a partition table, information about Spans and Stripes of AIX LVM, HP-UX LVM
Indication of Drobo volumes, HP EVA, HP LeftHand, Symphony SAN, HPE 3PAR etc.
Hexadecimal viewer for storages, partitions, files, file fragments
Field highlighting
Data interpreter
Parity calculator
Storage content comparison
Bitwise "exclusive OR" (XOR/Parity) function
Parallel search
Data allocation tracing through address translation
Tracing of data to files through reverse address translation
View of file fragments with virtual offsets and sizes
Hexadecimal editor for storages and partitions
Secure erasure of data from the storage (overwriting with zeroes, including with the help of an entropy map, SCSI format)
Direct interaction with SCSI devices using raw SCSI commands
Direct interaction with (S)ATA devices using raw ATA commands with support of some USB bridge chips
SCSI commander tool to issue any custom SCSI command (unlock, format etc.)
Supports remote access to iSCSI targets created with UFS Explorer (Network RAID, Professional, Technician) and other third-party iSCSI targets.
Embedded iSCSI Target (server) can provide remote access to the assembled volumes to iSCSI clients (initiators).
Software can mount an assembled volume as a local virtual SCSI disk to share access to the data to OS or third-party software (using iSCSI).
Pausing the scan
Previewing intermediate scan results
Saving scan state at any point as a "checkpoint" to return to
Saving scan results for further work
Full-range storage scan for all-at-once data recovery
Visualization of the scanning process
Five options for handling the existing file system
Automatic detection of lost partitions
Search for lost partitions
Defining partitions manually
Automated partition aligning
Interactive HTML report
Basic list of folders and files (HTML, CSV, XML)
Extended report on files and folders with the possibility of file integrity control (hash value, metadata test)
Report on file fragments
Recoverable data size with metadata test
Software events log
Main functional differences to UFS Explorer Professional Recovery
Compatible additional components (plugins)

Data recovery plugin for Dell EqualLogic is designed to automate the assembly and provide straightforward access to volumes on Dell EqualLogic Storage Arrays.

Data recovery plugin for HP StorageWorks EVA facilitates data recovery operations on HP Enterprise Virtual Arrays (EVA) by automating the reconstruction of Vraid array configurations and providing prompt access to the virtual volume content.

Data recovery plugin for HPE MSA assists in retrieving lost data from HPE Modular Storage Arrays (MSA), eliminating the manual effort required to assemble the storage pool configuration and obtain access to the available virtual volumes.

Data recovery plugin for HPE 3PAR StoreServ helps to recover lost data from 3PAR StoreServ storage systems of HPE. It automates the assembly of storage pool configurations and provides unimpeded access to the content of virtual volumes, removing the need for manual manipulations.

Data recovery plugin for Infiniti SAN aids in the recovery of data lost from storage systems relying on the Infiniti SAN ("Engenio") technology, including Dell PowerVault MD3 series, IBM DS3 series and NetApp E-series. It simplifies the recovery process by automating the assembly of storage pool configurations and grants immediate access to virtual volumes, which would otherwise require extensive manual operations.
Key features
 Support for forensic and other disk images
Support for forensic and other disk images
 The possibility to prove the forensic reliability of data
The possibility to prove the forensic reliability of data
 Plenty of other reporting options
Plenty of other reporting options
 Wide spectrum of supported storage technologies
Wide spectrum of supported storage technologies
 Controlled disk reading procedure
Controlled disk reading procedure
 Advanced disk imaging possibilities
Advanced disk imaging possibilities
 Multiple types of scanning
Multiple types of scanning
 Support of DeepSpar Disk Imager
Support of DeepSpar Disk Imager
 Interaction with MRT data recovery systems
Interaction with MRT data recovery systems
 Broad set of tools for efficient data analysis
Broad set of tools for efficient data analysis
When to use UFS Explorer Technician
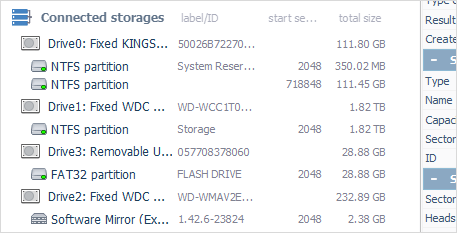
The utility effectively works with various linear storage devices, including internal as well as external hard disk drives, USB flash drives, memory cards and many others, thus serving as an essential data recovery tool for handling most typical cases of data loss, like accidental deletion of files, storage formatting, malware attack, hardware or software malfunction, etc.
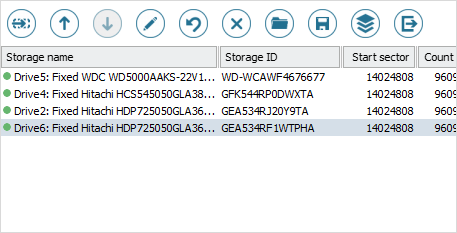
UFS Explorer Technician is an efficient solution for restoring data from RAID of different complexity, both software and hardware, and various RAID-based storages, like DAS, NAS and SAN. Moreover, the software makes it possible to perform data recovery from systems that apply specific RAID configurations, like Drobo BeyondRAID, Synology Hybrid RAID, Btrfs-RAID, ZFS RAID-Z, Dell EqualLogic and HP MSA with diagonal XOR.
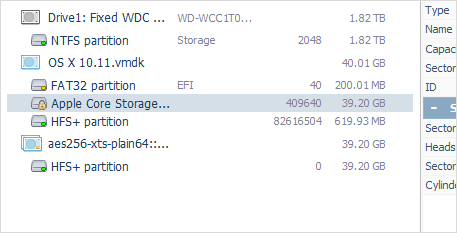
The software is enhanced with wide support of modern storage technologies employed in different environments. It allows processing composite volumes, including Apple Core Storage, LVM with thin provisioning, MS Storage Spaces and Dynamic Disks, deduplicated NTFS and ReFS partitions, SCSI/SAS-drives with non-standard sector sizes, QNAP NAS with enabled automated tiering (Qtier technology), etc. which significantly expands the list of target devices it can be applied to.
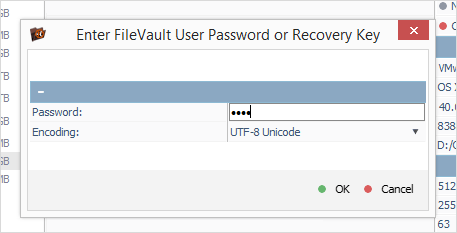
The application is able to decrypt volumes and directories for data recovery and data access purposes (if the encryption key is known). The list of supported methods includes LUKS, VeraCrypt (TrueCrypt), FileVault 2, BitLocker, encryption of Apple APFS volumes and eCryptFS.
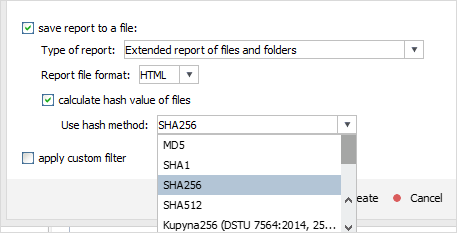
The program is able to generate an extended report on the data which may be particularly beneficial for forensic experts. Such a report contains the list of available files, their properties, checksums calculated for them using the chosen hashing algorithm together with the information about the scanned storage, the date of the scan and the time when the report was created.
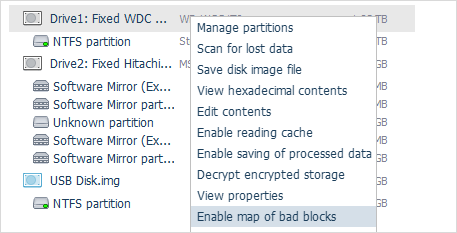
The application gives the possibility to recover data from storages that have damaged sectors or other hardware issues with maximum efficiency. Not only it offers highly configurable disk reading and imaging procedures, but also generates a map of bad blocks during the imaging process. In addition, virtual bad blocks can be defined dynamically on disk images by recognizing a given pattern or by reading bad sectors maps created by other compatible solutions. The software also allows converting the used or free file system space to a mask with emulation of defects and use it for imaging/scanning. Bitmap-based imaging via DeepSpar DDI is supported by the program as well.
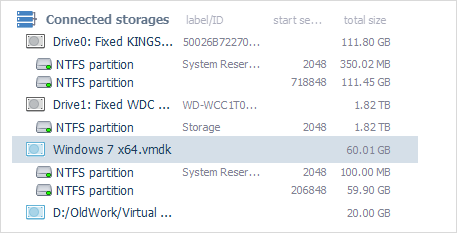
UFS Explorer Technician effectively deals with disk images and virtual disks created by major virtualization software, like VMware, Microsoft Hyper-V, VirtualBox, QEMU, XEN, etc. and successfully copes with data recovery from such storages as though they were ordinary physical devices.
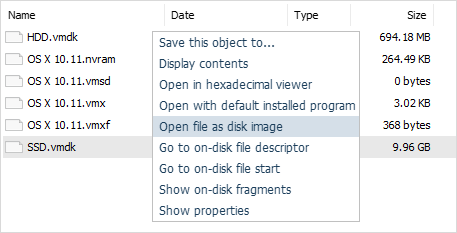
The software is capable of imitating work of virtualization software and consequently provides access and restores files from multi-level virtual storages with no additional operations required. For example, the user can scan a virtual disk stored inside another virtual disk and promptly retrieve files that were lost or deleted from it.
A set of tools integrated into the software allow effectively solving practically any case of logical data loss, including the most severe ones. The program will either simply read file system metadata or conduct its detailed analysis and predict the allocation of files based on the file system specifics, allocation of other files or file content analysis to produce the best possible data recovery result.
