Professional UFS Explorer software
is targeted at professional environments, where the diversity and complexity of involved storage systems, combined with non-trivial scenarios and the demand for vast customization, often fall outside the scope of typical data recovery solutions.
This set of products has been designed for the most demanding category of users, such as data recovery specialists and experts in digital forensics, who naturally have higher expectations from the software tools they use for work. Considering the challenges they regularly face in their professional activities, they need software that could offer much broader technological possibilities, expanded configuration options and more precise control over the recovery process when compared to standard solutions. Developed by industry experts who themselves have extensive practical experience in logical data recovery, UFS Explorer is tailored to meet the rigorous requirements of technicians occupied in this field, including those dealing with extremely elaborate storage systems, like server-based architectures and SANs.
Professional-grade UFS Explorer products are represented by two distinct editions: UFS Explorer Professional Recovery and UFS Explorer Technician. Both editions share their core functionality, but the Technician one is additionally equipped with specialized tools and capabilities to better address some peculiar data recovery scenarios, such as reconstruction of specific storage configurations, which is also reflected in the product’s licensing and pricing. Therefore, professionals can choose a product that best corresponds to their technical demands and available budgets.
Those seeking to compare the features of these editions may refer to the detailed comparison table, providing clear insights into the unique advantages of the two utilities.
Instant data access and profound scanning
UFS Explorer makes it possible to open intact data instantly, regardless of the underlying storage type, eliminating the need for time-consuming scans. And not only does it cover the most popular file systems, like FAT/FAT32, exFAT, NTFS, APFS, HFS+ or Ext4. The software is also able to process less common formats, including:
- ReFS
- XFS
- Btrfs
- ZFS
- F2FS
- UFS
- ReiserFS
- VMFS
- VMFS6
- NWFS
- NSS
- NSS64
- HFS
- HPFS
The Technician edition stands out in this respect with its unmatched file system support, enabling it to read from QZFS (QNAP QuTS hero), WAFL versions 2 to 4 (NetAPP ONTAP), Legacy JFS1 and JFS2 (AIX), VxFS4, VxFS6, VxFS7 (current Unix), EAFS, HTFS, DTFS (Older Unix) and NxFS (Urive).
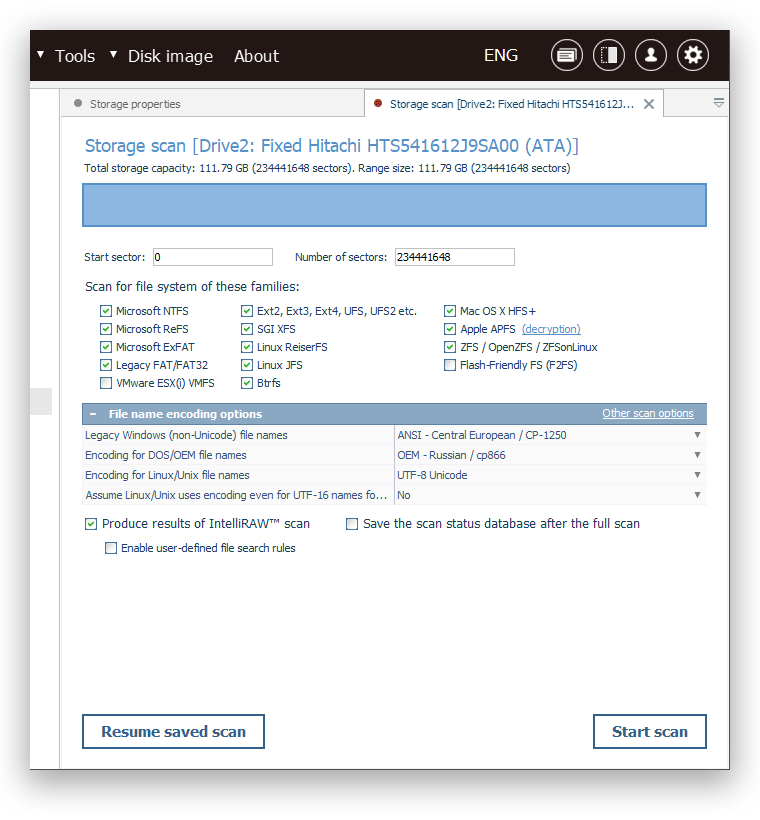
When it comes to searching for lost files or recovering data from damaged volumes, UFS Explorer offers here maximum flexibility. It allows conducting a full deep scan to recover every possible piece of data, defining custom IntelliRAW rules in order to improve the scan accuracy or choosing one of multiple tailored scan options to focus only on what’s necessary. Moreover, the programs enable users to save the intermediate state of a scan, pause and resume the operation at their convenience and save its results for future use.
Comprehensive handling of disks, disk images and virtual disks
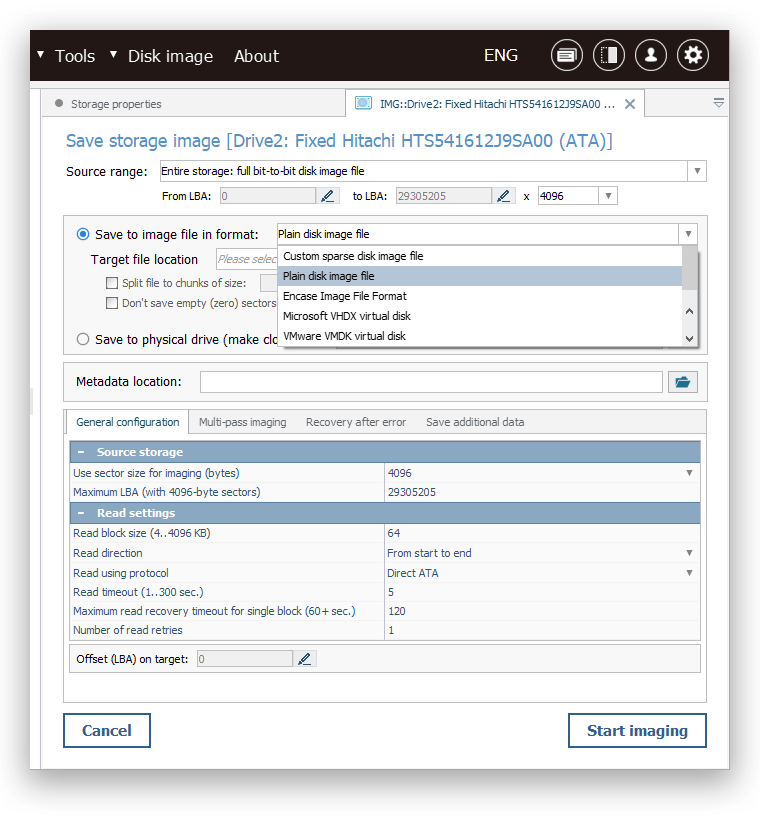
UFS Explorer is equipped with a robust suite of tools that allow specialists to work with physical storage media, disk images and virtual disks in an advanced manner and across various storage environments. The software includes a dedicated instrument for creation of disk images, including ones in forensic formats, ensuring that data is captured as efficiently as possible and preserved in its original state, while the resulting image can be freely utilized for further forensic analysis or in legal procedures. There is also a "read-once" option that helps to minimize the stress on unstable storage devices by avoiding multiple read requests to the same physical disk location and saving the accessed data directly to a sparse image file.
Beyond traditional disks, UFS Explorer enables technical experts to retrieve data from a variety of virtualized storage sources. It supports virtual disks of leading virtualization systems and a wide range of disk image formats, including those commonly used by forensic investigators. The user can interact with their data straightaway, without needing to extract or convert the file, even when it is stored on a RAID set or nested within a virtual machine.
- VMware
- Hyper-V
- VirtualBox
- QEMU
- XEN
- Apple DMG
- Apple sparsebundle
- Parallels
- EnCase
- AFF4
The Technician edition of the software further distinguishes itself with the unique ability to transcode sector sizes, producing full disk images for disks formatted with non-standard sector configurations, like 520 bytes used in HPE, EMC, NetApp, IBM and other systems. Thanks to this feature, it becomes possible to apply post-processing techniques and perform effective analysis of extended sector data even when dealing with such unconventional storage devices.
Decryption of encrypted data carriers
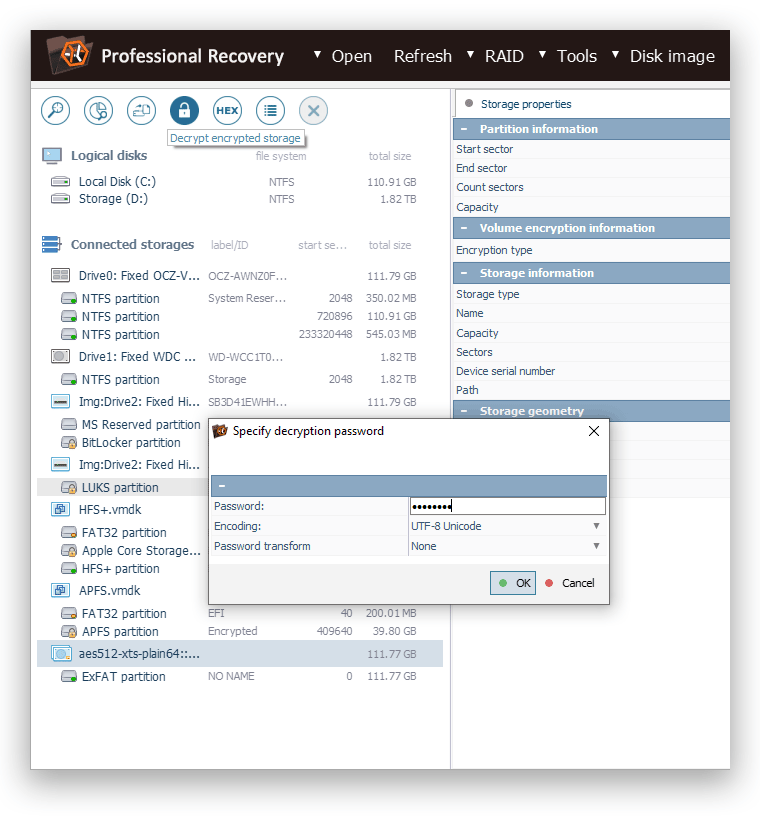
UFS Explorer features extensive decryption capabilities, making it an essential solution for accessing data stored on encrypted devices, volumes and file systems. The software supports both hardware- and software-based encryption, ensuring that diverse security mechanisms can be handled with ease when the correct credentials are known to the user.
The programs allow unlocking digital media protected at the hardware level. This includes drives from WD MyBook/MyPassport devices with a variety of bridge chips (JMicron JMS561, Symwave SW6316, etc.) and a selection of drives secured with ATA passwords (the password must be available, along with padding and transformation).
For software-based encryption, UFS Explorer is equipped to decrypt volumes ciphered by popular technologies like BitLocker, LUKS, VeraCrypt, Apple APFS and FileVault 2. Furthermore, the applications support the eCryptFS file system level encryption, enabling the decryption and recovery of individual folders and files not only within Linux distros, but also on NAS shares, such as Synology, QNAP, Asustor, TerraMaster and others. Aside from that, the programs address specialized encrypted virtual disk and disk image formats, for example, VMDK files of VMware or DMG and sparsebundle files of macOS.
- LUKS
- FileVault 2
- Encrypted APFS
- BitLocker
- TrueCrypt
- VeraCrypt
- OpenBSD BIO
- Encrypted VMDK
- Encrypted DMG
- Encrypted sparsebundle
- JMicron JMS561
- Symwave SW6316
- Initio 1607E
- JMicron JMS538
- Oxford OXUF943SE
- eCryptFS
Extensive RAID support
UFS Explorer helps to ensure effective data recovery from a broad spectrum of RAID configurations, covering both classical software and hardware RAID setups, as well as more intricate RAID-based storage technologies.
As for standard RAID, the software supports most widely implemented patterns, including RAID 0, RAID 1E, RAID 3, RAID 5, RAID 6 and RAID 7. The same goes for nested RAID levels, like RAID 10, RAID 50, RAID 60 and RAID 50E.
Besides traditional RAID, the programs can process many advanced RAID-like virtual systems. This includes such specific configurations as ZFS RAID-Z, Btrfs-RAID, Drobo's BeyondRAID, Synology’s Hybrid RAID, Apple’s Software RAID and Core Storage, Linux LVM with Thin Provisioning and many other implementations.
Most complex volumes can be assembled by the software automatically. Yet, when this procedure is disabled or the array’s metadata is severely damaged, UFS Explorer provides specialized tools for its manual reconstruction, like RAID Builder for traditional RAID sets, dedicated assistants for Drobo BeyondRAID and Microsoft Storage Space volumes, etc.
Another notable feature of UFS Explorer is the RAID decomposition tool, also known as "Reverse RAID". It allows users to break down an assembled virtual array into its individual components. By disassembling the RAID structure, experts can open and examine each produced component independently. This functionality is particularly useful for rebuilding RAID with different parameters, for example, when migrating data from one RAID setup to another or creating a RAID set from a single regular disk.
- LVM
- LVM 2
- mdadm
- NT LDM
- Storage Spaces
- Apple Software RAID
- Core Storage
- Fusion Drive
- JMicron JMS561
- OpenBSD BIO RAID
- Intel Matrix
- DDF1
- DDF2
- Silicon Image
- ZFS RAID-Z
- Btrfs-RAID
- BeyondRAID
- Synology SHR
- Synology RAID-F1
- Reverse RAID
Work with various SAN systems
UFS Explorer is an indispensable assistant for professionals tasked with data recovery from complex SAN storage arrays. The Professional and Technician editions both support SANs with various RAID levels, including degraded RAID 5, RAID 10 and up to double-degraded RAID 6 and RAID 60. For volume reconstruction, the software can utilize external data maps created through conversion of volume metadata.
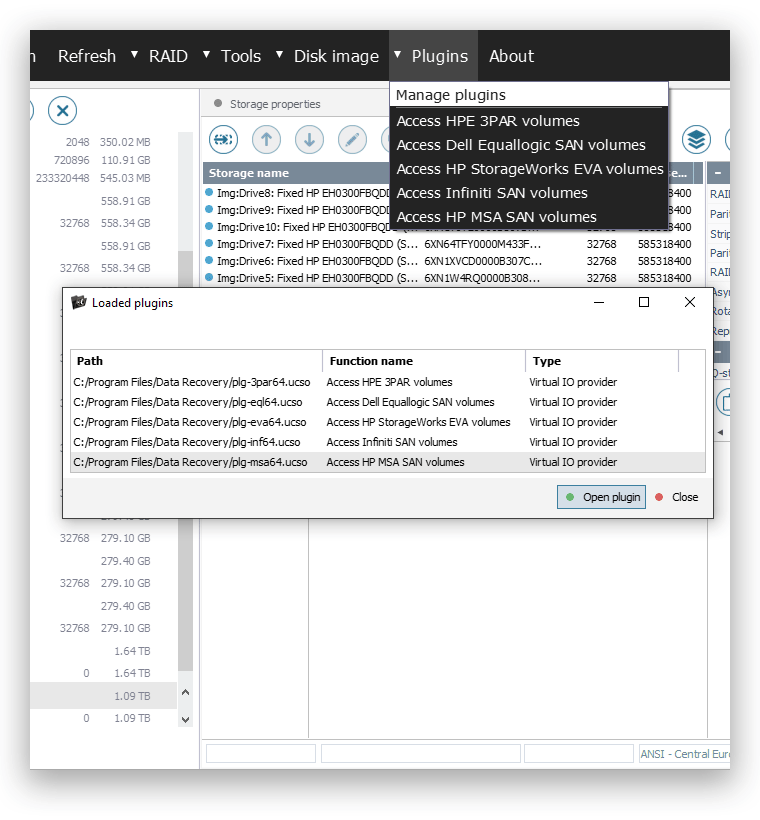
For more advanced SAN support, the Technician edition can be completed with specialized plugins. These plugins automate the assembly of particular SAN storage configurations and provide direct access to their virtual volumes, eliminating the need for laborious manual analysis. The available assortment of plugins includes:
- Plugin for Dell EqualLogic Storage Arrays;
- Plugin for HP StorageWorks EVA;
- Plugin for HPE Modular Storage Arrays (MSA);
- Plugin for HPE 3PAR StoreServ;
- Plugin for SANs relying on the Infiniti SAN ("Engenio") technology, like Dell PowerVault MD3 series, IBM DS3 series and NetApp E-series.
Specialists can also develop their own custom plugins and integrate them into the program using a simple universal mechanism.
Networking, data sharing and other features
Apart from its key data recovery capabilities, UFS Explorer offers a range of extra features that enhance its value in professional settings.
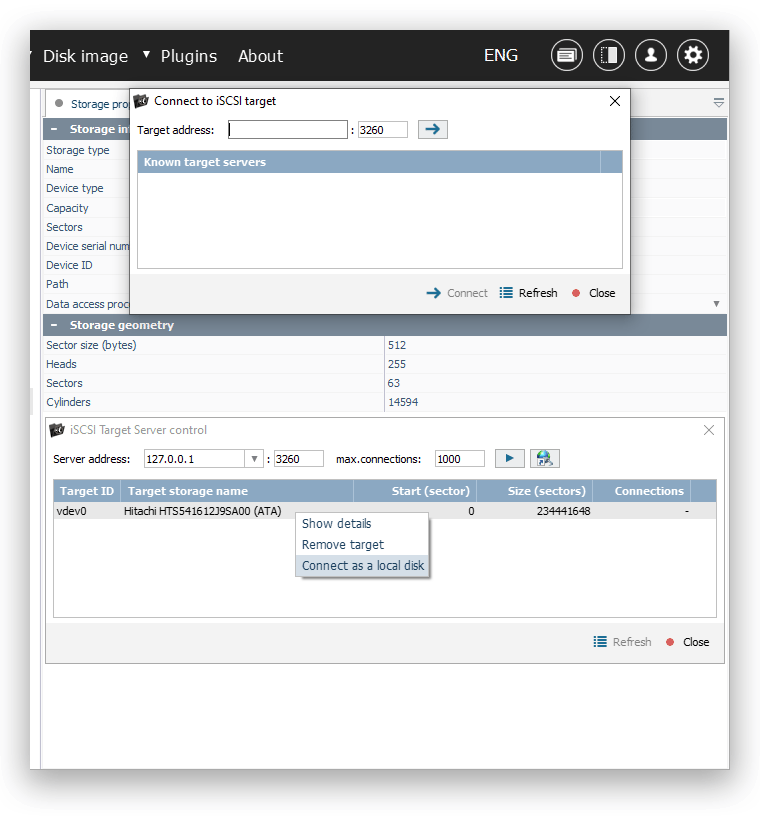
For instance, the software supports iSCSI, providing a built-in iSCSI client for remote access to native iSCSI targets (created within UFS Explorer of the Network RAID, Professional or Technician edition) as well as to various third-party SAN/iSCSI targets.
Moreover, UFS Explorer itself includes an embedded iSCSI target server, enabling other iSCSI clients to safely interact with the volumes reconstructed in the program. The software allows mounting an assembled volume as a local read-only virtual SCSI disk, making it accessible to the operating system or other applications, and, at the same time, protected from overwriting. This feature significantly simplifies further processing of such volumes using other tools, ensuring a smooth and efficient workflow.
Certain auxiliary features are exclusive to UFS Explorer Technician, like the ones facilitating low-level storage access. The program makes it possible to send specific SCSI commands to SCSI-based storage devices and supports direct communication with (S)ATA devices using raw ATA commands, including through some USB bridge chips. The SCSI commander tool further extends its functionality by allowing users to perform operations on drives with the help of custom SCSI commands, such as formatting or unlocking. There is also a tool for secure data erasure using an entropy map, created in the process of disk imaging and utilized to target only non-empty parts of the storage. With the help of this method, wiping can be performed much faster, especially when dealing with multiple drives. And once the data is dumped, the cleaned functional drives can be promptly reused instead of having to purchase new ones.