Virtual decomposition of RAID (reverse RAID) in UFS Explorer
Virtual decomposition of RAID (also referred to as "Reverse RAID") is a useful data recovery technique, especially when dealing with damaged arrays. It allows breaking down the RAID layout and access or recover data from its individual components, for example, in situations when the data on the physical drives is corrupted, but can be still restored using redundancy.
While most standard data recovery software is able to cope with basic RAID recovery scenarios, "Reverse RAID" is a more advanced feature that contrasts with the typical RAID assembly process. The Professional and Technician editions of UFS Explorer are designed for advanced data recovery tasks and do include support for "Reverse RAID". The software enables virtual decomposition of a complex or composite storage and makes it possible to access its components as if they were separate storage devices, without the need to interfere with the real configuration.
The feature is implemented in the programs via the "Decompose (reverse) RAID" tool available under the "RAID" section of the main menu.

To illustrate how it works, let’s take a RAID 5 configuration where one of the drives is missing. We need to reconstruct the data on the missing component and then copy it to another intact drive.
First of all, we have to recreate the original RAID 5 configuration in the software using the available drives or their disk images. The missing drive will be represented in the storage structure by a placeholder.
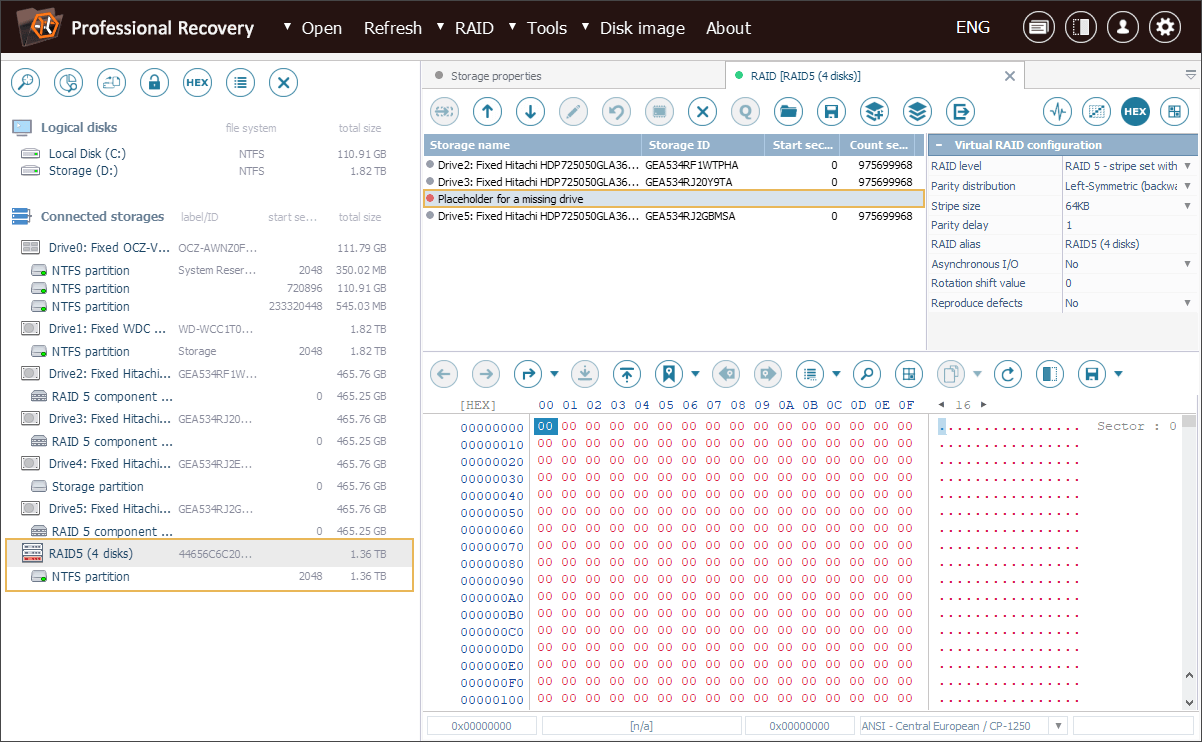
After that, we can go to the "RAID" menu and launch the "Decompose (reverse) RAID" tool.
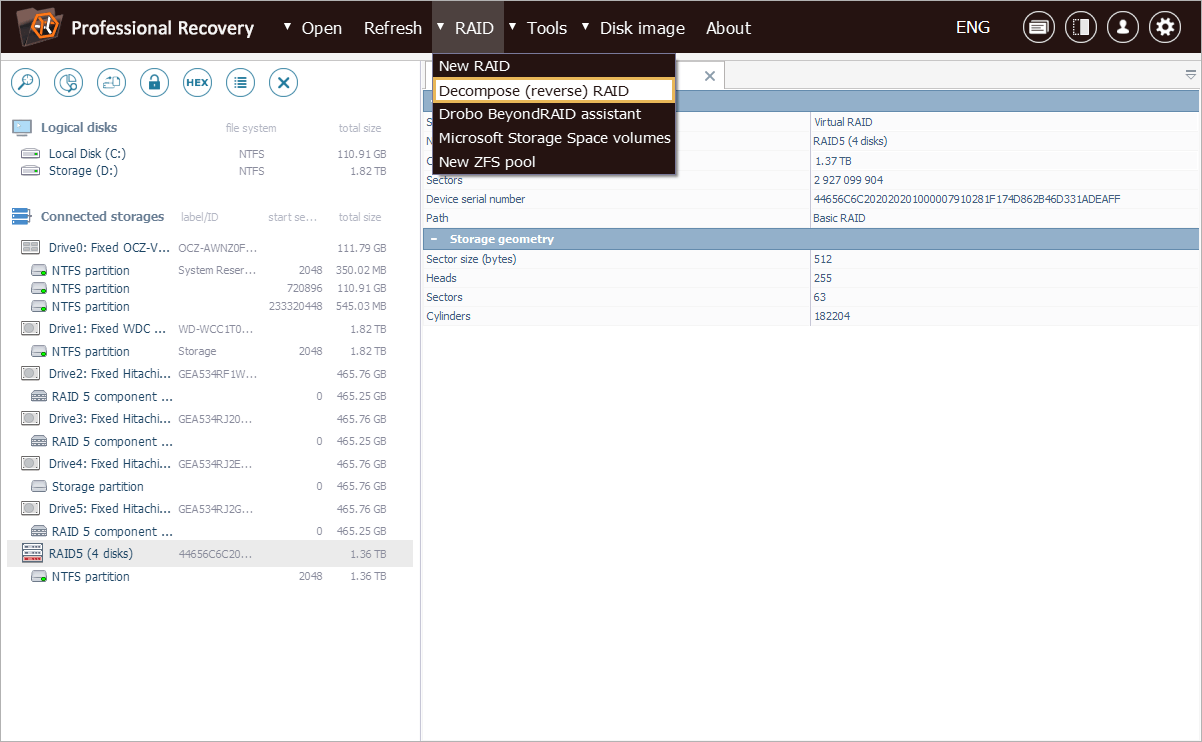
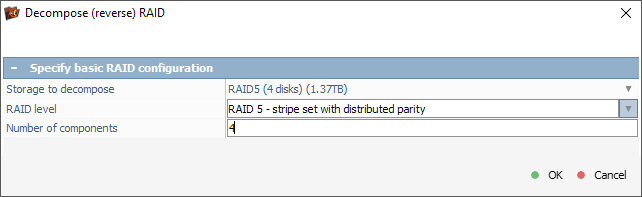
In the opened dialog, we need to choose our RAID set from the drop-down menu next to the "Storage to decompose" property, specify the RAID level and the number of drives in the configuration.
Once we click "OK", the software will show the list of extracted components. Any of them can be instantly mounted in the storages navigation pane using the "Open component as storage" option.
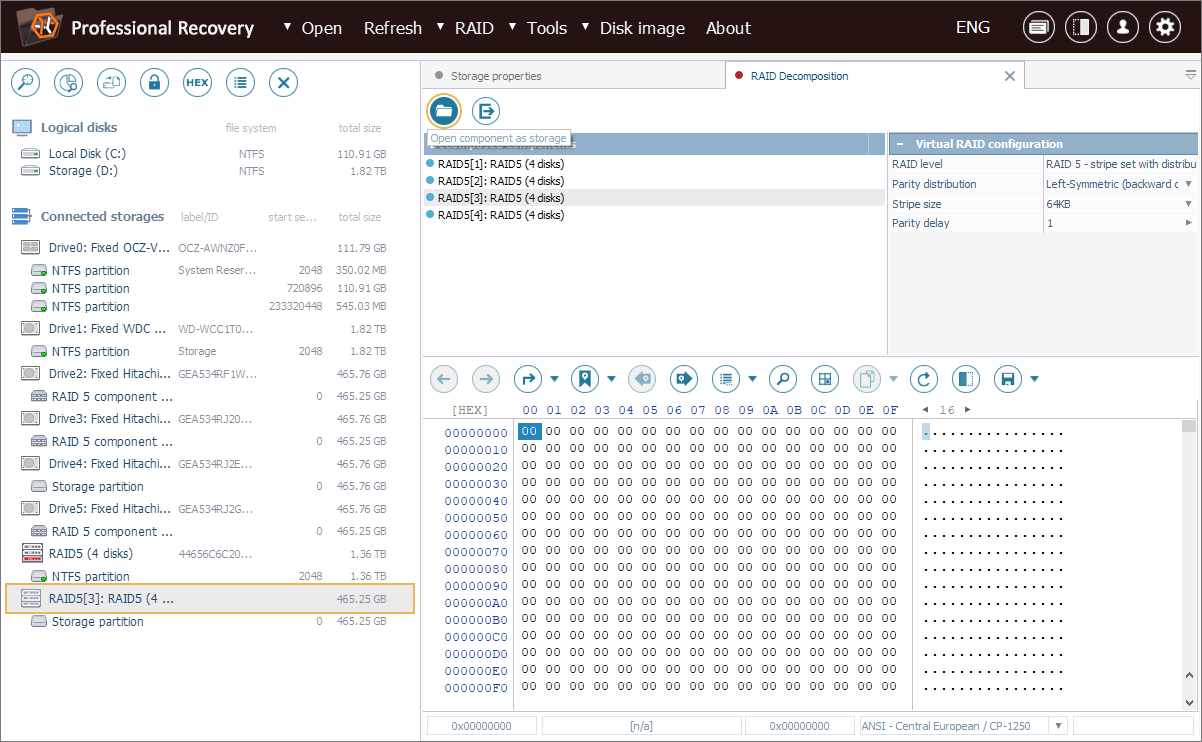
After that, this component can be processed in the software as an individual storage, for example, imaged or opened in Hexadecimal Viewer for further analysis.
Last update: March 11, 2025
